Ricochet is the best place on the internet to discuss the issues of the day, either through commenting on posts or writing your own for our active and dynamic community in a fully moderated environment. In addition, the Ricochet Audio Network offers over 50 original podcasts with new episodes released every day.
 Kompromat
Kompromat
How FANCYBEAR hacked Podesta’s Gmail (as well as Powell’s, Breedlove’s, and many hundreds more) — linking the DCLeaks, G2 and Wikileaks ops. From https://twitter.com/ridt.
I can’t recall which thread gave rise to this question, but I remember that some of you wanted to know what evidence there was that Russia was behind the DNC hack.
Thomas Rid, a professor in the Department of War Studies at King’s College London, is among other things the author of “Attributing Cyber Attacks,” which he wrote for the Journal of Strategic Studies in 2015. He’s written a very clear and readable article for Esquire about Putin, Wikileaks, the NSA and the DNC e-mail hack. It won’t take you but ten minutes to read, but I’ll pull out some of the highlights:
According to Reuters, the FBI first contacted the DNC in the fall of 2015, obliquely warning the Democrats to examine their network. It wasn’t until May, however, that the DNC asked for help from a cybersecurity company called CrowdStrike, which had experience identifying digital espionage operations by nation-states. CrowdStrike immediately discovered two sophisticated groups of spies that were stealing documents from the Democrats by the thousands.
CrowdStrike was soon able to reconstruct the hacks and identify the hackers. One of the groups, known to the firm as Cozy Bear, had been rummaging around the DNC since the previous summer. The other, known as Fancy Bear, had broken in not long before Putin’s appearance at the St. Petersburg forum. Surprisingly, given that security researchers had long suspected that both groups were directed by the Russian government, each of the attackers seemed unaware of what the other was doing.
If you’d like a closer look at what Crowdstrike found, they blogged about it — having been authorized to do so by the DNC, I assume, for obvious political purposes.
Meanwhile, a Twitter account associated with a site called DC Links started linking to Gen. Philip Breedlove’s private conversations. (You may recall that Breedlove, until recently the supreme commander of NATO forces in Europe, testified before Congress last February that Russia posed an “existential threat” to the West. Since Moscow’s seizure of Crimea, Breedlove has been one of Putin’s most vocal critics.)
On June 14, less than an hour after The Washington Post reported the breach at the DNC, CrowdStrike posted a report that detailed the methods used by the intruders. The firm also did something unusual: It named the Russian spy agencies it believed responsible for the hack. Fancy Bear, the firm said, worked in a way that suggested affiliation with the GRU. Cozy Bear was linked to the FSB.
But a hacker who called himself Guccifer 2.0 demurred, claiming to be solely responsible for the attacks. Guccifer offered a large batch of documents to journalists to substantiate his claim.
As soon as Guccifer’s files hit the open Internet, an army of investigators—including old-school hackers, former spooks, security consultants, and journalists—descended on the hastily leaked data. Informal, self-organized groups of sleuths discussed their discoveries over encrypted messaging apps such as Signal. … The result was an unprecedented open-source counterintelligence operation: Never in history was intelligence analysis done so fast, so publicly, and by so many.
Matt Tait, a former GCHQ operator, immediately found an anomaly. One of the first leaked files had been modified on a computer using Russian-language settings. He tweeted an image of the document’s metadata settings. Researchers also discovered that the malware used to break into the DNC was controlled by a machine that had hacked the German parliament in 2015. German intelligence traced the breach to the Russia’s Main Intelligence Directorate, the GRU — also known as “Fancy Bear.”
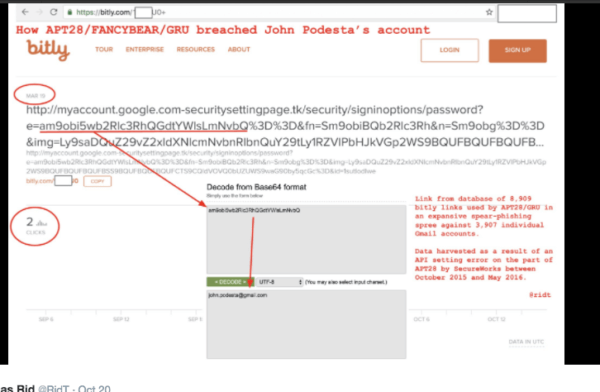
There was more evidence linking the files to Russia, including the use of a distinctive Russian emoji. But the key evidence came from the hackers’ spear-phishing emails. They had used the URL shortener Bitly to shorten the bait, but they’d neglected to set two of their accounts to “private.”
As a result, a cybersecurity company called SecureWorks was able to glean information about Fancy Bear’s targets. Between October 2015 and May 2016, the hacking group used nine thousand links to attack about four thousand Gmail accounts, including targets in Ukraine, the Baltics, the United States, China, and Iran. Fancy Bear tried to gain access to defense ministries, embassies, and military attachés. The largest group of targets, some 40 percent, were current and former military personnel. Among the group’s recent breaches were the German parliament, the Italian military, the Saudi foreign ministry, the email accounts of Philip Breedlove, Colin Powell, and John Podesta—Hillary Clinton’s campaign chairman—and, of course, the DNC.
Rid then explains why, in the view of the researchers who worked on this, the GRU’s tradecraft was so sloppy. (It tightened up after this. When files next appeared, they were scrubbed of this kind of metadata.)
“The operators behind Guccifer and DC Leaks,” he writes,
appear to have recognized that American journalists were desperate for scoops, no matter their source. The Russians began to act like a PR agency, providing access to reporters at Politico, The Intercept, and BuzzFeed. Journalists were eager to help. … The most effective outlet by far, however, was WikiLeaks. Russian intelligence likely began feeding hacked documents to Julian Assange’s “whistleblower” site in June 2015, after breaching Saudi Arabia’s foreign ministry.
His discussion of the NSA hack — a far more difficult breach to pull off — is very worth reading in full. The connection is this:
American investigators had long known that the Russians were doing more than spear-phishing, but sometime around April they learned that the intruders were using commercial cloud services to “exfiltrate” data out of American corporations and political targets. Cozy Bear, the hacking group believed to be affiliated with the FSB, used some two hundred Microsoft OneDrive accounts to send data from its victims back to Moscow.
Using cloud services such as OneDrive was a clever but risky move—it was a little like taking the bus to make off with stolen goods from a burglary. Though the widespread use of the services by legitimate users offered a degree of cover for the hackers, data provided by Microsoft also helped America’s elite digital spies identify the DNC intruders “with confidence” as Russian. It is even possible that the U. S. government has been able to identify the names and personal details of individual operators. The Russians knew they’d been caught.
When WikiLeaks published the first batch of Podesta’s emails, the US intelligence community publicly declared itself “confident” that Russia’s “senior most officials” had authorized the hack:
The U.S. Intelligence Community (USIC) is confident that the Russian Government directed the recent compromises of e-mails from US persons and institutions, including from US political organizations. The recent disclosures of alleged hacked e-mails on sites like DCLeaks.com and WikiLeaks and by the Guccifer 2.0 online persona are consistent with the methods and motivations of Russian-directed efforts. These thefts and disclosures are intended to interfere with the US election process. Such activity is not new to Moscow—the Russians have used similar tactics and techniques across Europe and Eurasia, for example, to influence public opinion there. We believe, based on the scope and sensitivity of these efforts, that only Russia’s senior-most officials could have authorized these activities.
The intelligence community declined to explain how they reached their conclusion, but it’s reasonable to assume they have data we can’t see. That said, the data harvested by SecureWorks is publicly available. And this, Rid writes, “makes it clear that Fancy Bear broke into the Clinton chairman’s account as early as late March.”
Trump was briefed about this. Despite this, he said during Thursday’s debate that “Our country has no idea” who was behind the hacks. I don’t know if Hillary Clinton was correct to say that 17 intelligence agencies have concluded Russia was behind them, but she probably is — and it is certainly not true that we have no idea.
Motherboard is also running a well-written, clear article about the evidence, with screenshots of the malicious Bitly URLs. They interviewed Rid for the article: “We are approaching the point in this case where there are only two reasons for why people say there’s no good evidence,” Rid said. “The first reason is because they don’t understand the evidence—because the don’t have the necessary technical knowledge. The second reason is they don’t want to understand the evidence.”
Published in General, Science & Technology




I’d feel better about your analogy if there were a Lincoln, a Grant, and a Sherman somewhere on the horizon. All I’m seeing is Buchanans and McClellands.
I guess we’ll see.
No, I think the anti-nuclear movement that was begun by the KGB to stop us from putting nuclear weapons in Europe is the best. It is still going strong and crippling nuclear power. The idiots who think global warming is real still hate nuclear power which would be their salvation. That, of course, assumes they believe their own BS.
Except it didn’t work. NATO deployed GLCMs and Pershing IIs despite the Freeze Movement. We had leaders back then, not community organizers and other Alinskyite thieves. This operation will work and they will own us.